
• Motor/Automobile Associations
• International Advocacy Groups
• Conservation Groups
• Publishing Companies
• Non-Profit Organizations/Foundations
• Insurance & Financial Services
• Government Agencies
• Healthcare Services Industry
• Variety of Social Clubs & Organizations
• Outsource Business Processing
• Full-Service Fulfillment Services
• AMC’s and many more…
Our Systems are customizable. Our platform can be tailored to meet your specific business needs.

Our systems are flexible. Our capabilities grow and evolve with your business needs.

Our systems are scalable. Our platform can accommodate the needs of any size organization.

Our systems are secure. Our security protocols meet or exceed all security requirements.

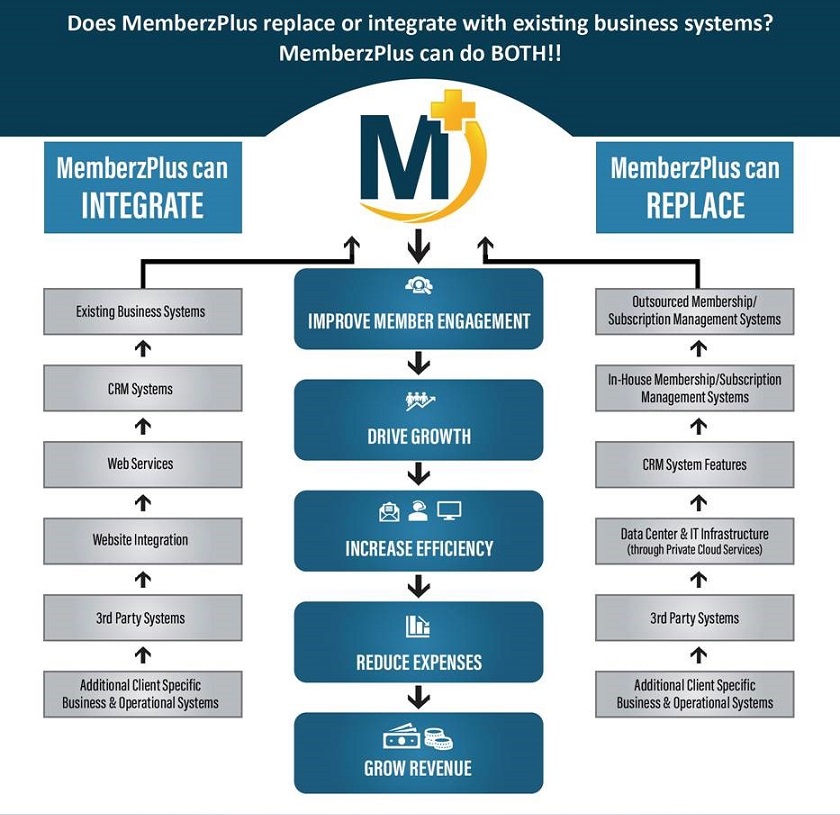
Whether you are actively looking for a new membership or subscription management solution or considering it within the next 3 years; we can assist now.
We offer a complimentary analysis service to assist in analyzing your operational effectiveness, identify areas to improve efficiency, help you build internal consensus on priorities, and offer solutions tailored to your specific business requirements.
Schedule Your Complementary Analysis Today!